Advanced Security Measures (#13)

Digitization, standardization, and the electronic exchange of research data are all very effective in improving research practices. However, this also makes it easier for systems to be breached from any one of the many access points. Here we will discuss a key method to safe guard your data from hackers.
Dual Factor Authentication
Dual factor authentication or two-factor authentication is a process used to verify the users’ identity when logging into a website or application.
2FA Provides a higher level of security than a single factor authentication.
How you can set up 2FA

First make sure to grab your phone and your computer. Then using your computer login to your UKA email.
Using your phone, you can download any authenticator app of your choosing.

Image taken from www.twilio.com
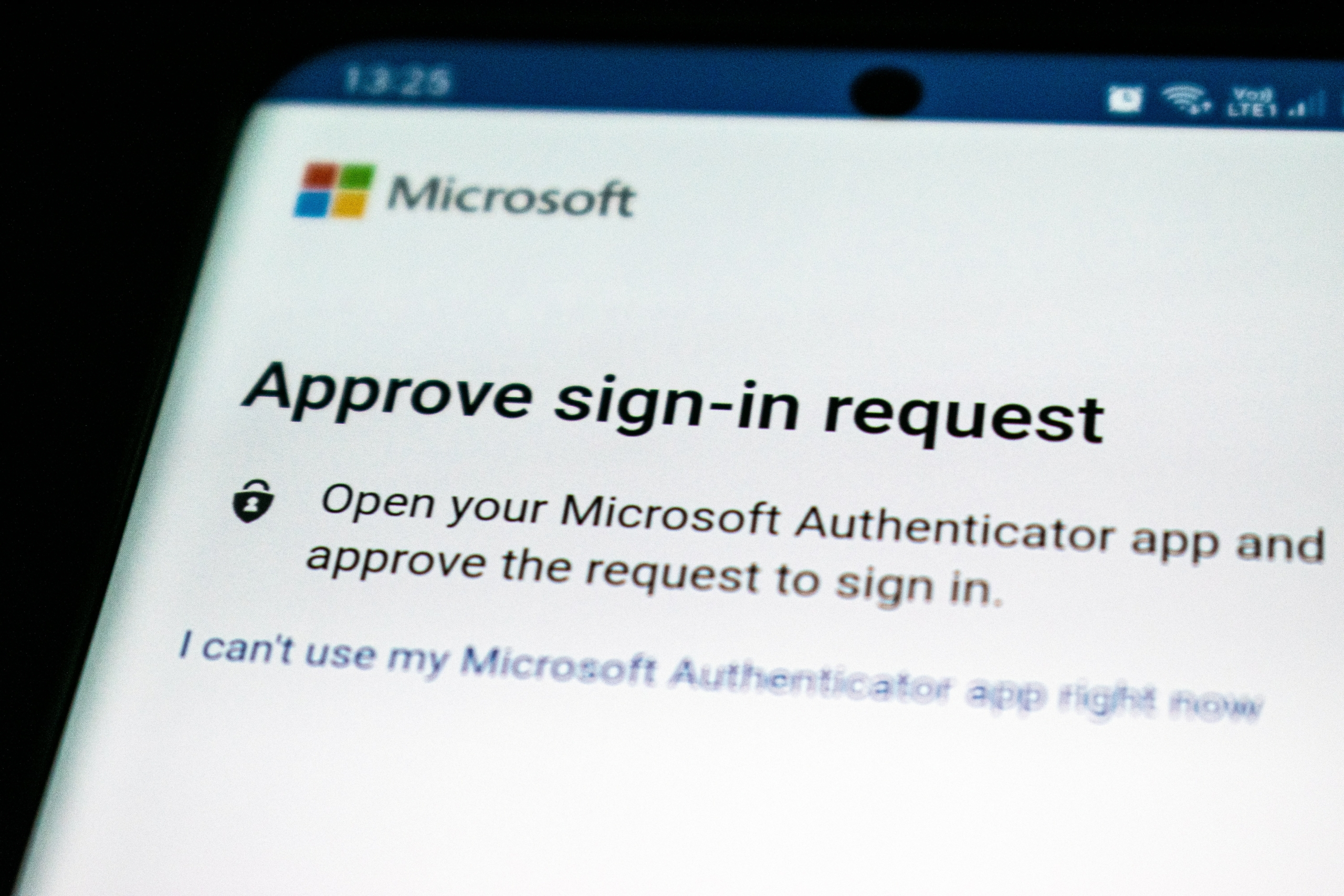
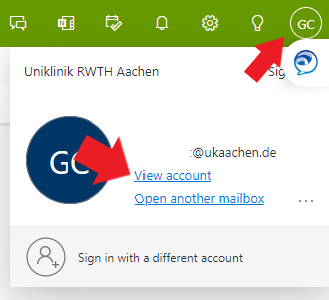
Moving back to your computer. In your email window, click on ‘View Account’
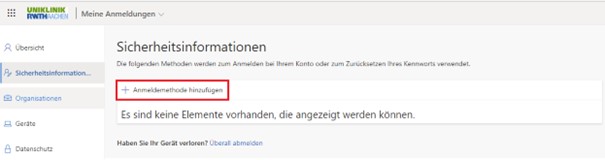
As seen in the image below, click on ‘Security information’ or ‘Sicherheitsinformationen’ then click on ‘Add sign-in method’ or ‘Anmeldemethode hinzufügen’
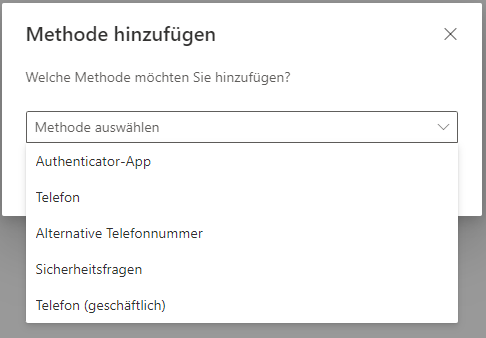
A drop down box will appear with several options including the choice of an authenticator application. Click on ‘Authenticator Application’ as seen in the image on the right and click on ‘next’
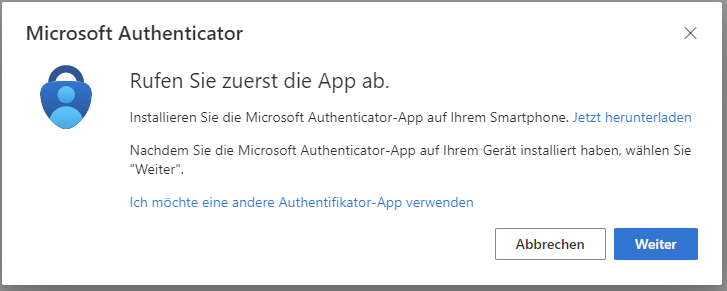
A window will appear to notify you to download the Microsoft Authenticator App or you can click on the ‘I want to use a different authenticator app’ depending on your preference
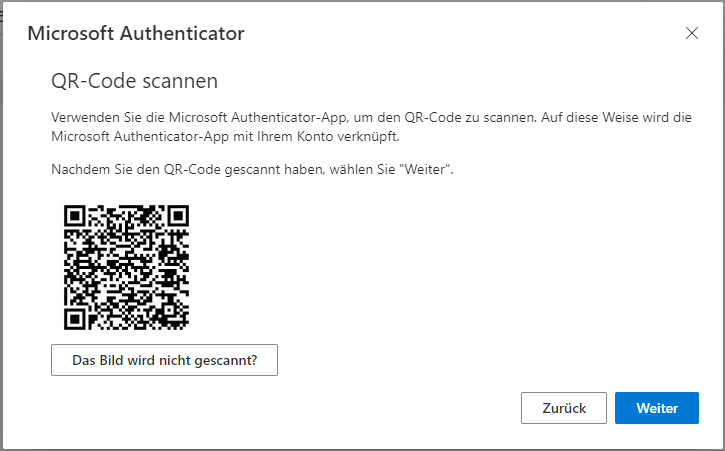
Regardless of your choice of authenticator app once you click ‘next’ a QR code will appear for you to scan it with the app of your choice on your phone.
Lastly, just follow the prompts on your phone to complete the 2FA setup
Keep In Mind!
While 2FA provides the user with greater cybersecurity. It is also vital to use complex passwords. For more information on improving and managing passwords see RDM Newsletter #6

